The business of monitoring, measuring and understanding social media
Brand Monitoring on the Deep and Dark Web
This is a guest post contributed by Webhose.
Traditionally, brand monitoring has relied primarily on social media analysis and open web monitoring to uncover as much information as possible about the brand, competitors, the product, or simply how to best engage the customer. Today, brand monitoring that relies on open web monitoring is no longer sufficient—it must include deep and dark web monitoring as well.
While the dark web includes content that is accessible to the public through special tools like the Tor browser, deep web content (like online banking portals and chat applications) is hidden to the public because it requires registration to gain access.
Proper deep and dark web monitoring can detect risks immediately when threats are identified, mitigating the damage to companies and their brands. Monitoring these sources, however, requires the ability to constantly access, identify and collect the immense amount of data that is being created on the deep and dark web every minute.
Dark web monitoring specifically is even more crucial, because that is where cybercriminals often execute more extreme crimes, the ones that can cause long-lasting impact to your brand.
Here are a few examples of how deep and dark web monitoring is crucial for today’s comprehensive brand monitoring, and how cybercriminals tend to migrate towards the dark web.
Chat Applications and their Relevant Groups
In the recent past, cybercriminals tended to focus their activities on the dark web marketplaces and networks that offered near anonymity. Today, they can find the same level of anonymity, a more user-friendly experience, and extensive language support in social media messaging apps and chat applications on the open web. Telegram, for example, is supported in 14 languages, and Discord in over a hundred.
Cybercriminals started to migrate to chat applications after the shutdown of popular dark web marketplaces such as Hansa and AlphaBay by law enforcement agencies in 2017. At the same time, these chat applications also started to offer end-to-end encryption, making it almost impossible for intelligence units to intercept. Today, many groups have options for invite-only groups, secret groups, deleting messages, and other precautions that help cybercriminals hide their activities from the public. Combining these features with a far better user experience and extensive language support had cybercriminals migrating to these chat applications in droves.
Here is an example of a specific Telegram channel dedicated to the subject of carding methods. Carding is a type of financial crime that steals financial data (such as credit card or bank account information) from individuals for illegal purposes.
This actor has started to share a new carding method of using stolen credit-card information to pay on e-commerce sites like Amazon. (Note that this post is from December 1, so the method may be quite new). This channel is only one out of dozens (if not hundreds) of channels that share and provide methods and services to commit similar frauds against e-commerce giants.
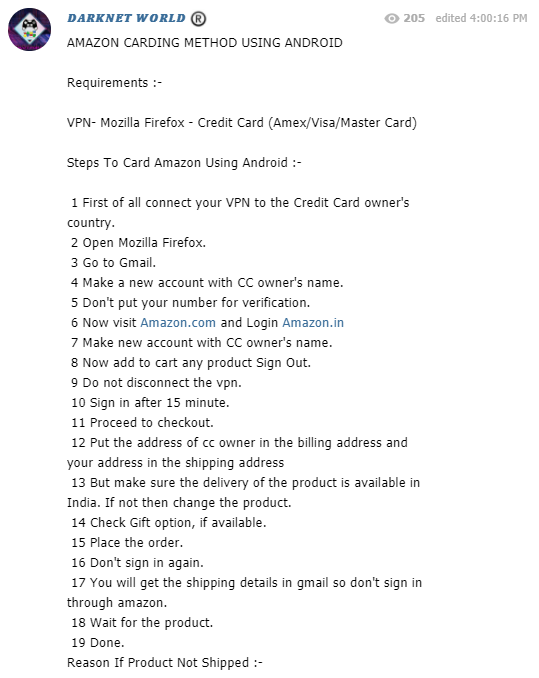
Post from Telegram channel sharing a new carding method with users from the Webhose Cyber Endpoint
Organizations that want to monitor their brand today need to not only monitor the different chat applications but make sure that they invest in deep and dark web monitoring resources that are able to identify the relevant chat groups.
Migration from Social Media to Chat Applications and the Dark Web
Just like e-commerce traders, the modern dark web vendor manages a few channels: two or three shops in a deep or anonymous network, or a few groups in chat applications to optimize traffic to their “shop.” Some provide their ID in a chat app so that they can be reached privately about selling their goods or services. It’s also a precaution: In the event that one channel or network is shut down, they can continue to operate from different channels. As a result of this new approach, one of the most effective methods of brand monitoring today includes the monitoring of dark web, social media and chat applications related to a specific activity or cybercriminal.
For example, Anonymous, a decentralized community of tech activists widely known for its various cyber attacks, operated a Twitter account in June. The Twitter account included an onion link to Anonymous Italy’s IRC web client server. When logged in long enough on this server, one can hear additional chatter of people associated with the Anonymous group. As of this publication, the account still exists and shares content.
Twitter account of Anonymous
Anonymous’ site on the IRC web client server found in the TOR network
Other hacktivist groups, such as the Pryzraky and Iznaye hacktivist groups from 2019, have active Facebook and Twitter pages where they broadcast their achievements and publicize their actions. Both groups are known for targeting and taking down government or company websites in the name of different causes.
Twitter account of Pryzraky
Suspended Twitter account of Iznaye
Checking the content in our repository, we were also able to find several mentions of the two groups and a few individual members in a Discord server. Users in this chat successfully left the channel before the content was added to the Cyber Endpoint coverage.
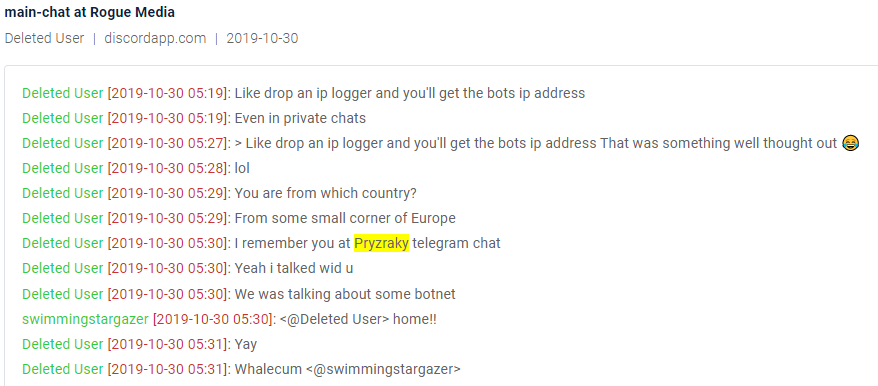
Chat from Discord in the cyber endpoint mentioning link to Pryzraky group
One of the members in Discord also declares that he was a member of the Iznaye cyber team.
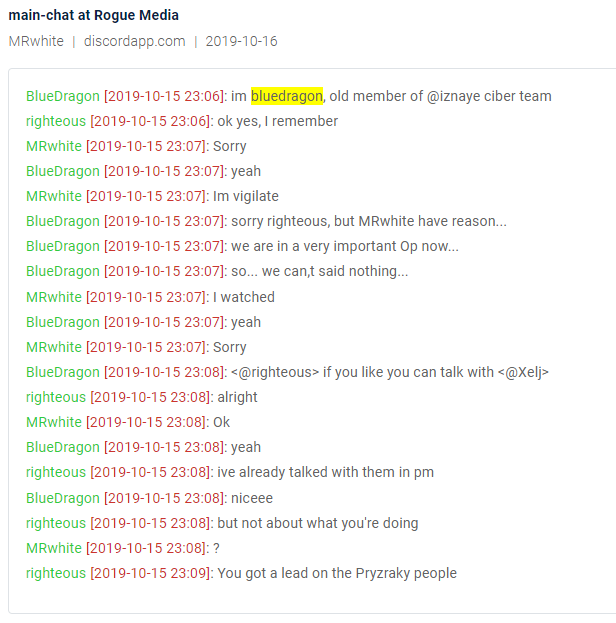
Chat from Discord in the cyber endpoint mentioning link to Iznaye group
Twitter is a mainstream source for cyber news, and cybercriminals use many other social media platforms in the open web as channels to communicate to their audience. Each has its own particular Terms of Service (TOS) stating the policy on monitoring. Dark web marketplaces and forums have fewer regulations. Out of the public eye, criminals communicating on dark-web channels tend to behave more freely.
Migrating from Open Web Forums to Dark Web Marketplaces
We can also see the migration of cybercriminals to the Tor network (the majority of the dark web) by taking a quick look at Reddit boards that used to be active, yet are now closed or banned.
Reddit, a major social network, used to host discussions about dark web markets and vendors in dedicated subreddits. Here are a few examples:
- https://www.reddit.com/r/DarkNetMarkets
- https://www.reddit.com/r/DNMSuperlist/
- https://www.reddit.com/r/darkmarket/
The first two subreddits discussed dark web marketplaces available in the Tor network and the goods sold in them. They were banned from Reddit, as the site explained: “due to a violation of Reddit’s policy against transactions involving prohibited goods or services.” The last one is a private subreddit, which means that in order to see content from this subreddit, one has to be approved by the moderators of the forum.

Instead of fighting the regulations and TOS of the social networks, cybercriminals found alternative forums with a lot of audience and traffic in the Tor network. For example, TheHub, Dread and DNMAvengers are forums that have been around for a few years and attract new marketplaces to post their announcements. Buyers write reviews of vendors on these forums, and market admins use them to provide more information about their marketplaces.
The Most Serious Threats to Brands Lie in the Deep And Dark Web
Companies should monitor chat applications for leaks and databases sold by individuals. But cybercriminals often prefer the dark web for the most nefarious acts.
For example, credit card leaks are another common crime exploited on the deep and dark web far more often than in social networks. Leaked credit cards are a huge part of brand monitoring in the banking sector, since any leaked credit card of the bank should be cancelled as soon as possible.
A quick search for the term “ccnum” in the mainstream social networks revealed:
- Twitter: The latest results that contain a leaked credit card number from October 7th.
- Instagram: No leaked credit cards were found, either by the keywords or the hashtag #ccnum.
That’s compared with the detection of more than 350,000 leaked credit cards over the past year, from chatting applications alone (such as Telegram, Discord, IRC and Whatsapp) in our repository. Many channels in these networks are dedicated specifically to sharing leaked credit card information, such as the “HackingwithAndroid” Telegram channel.
These channels are very popular for actors who use them to exploit the leaked data.
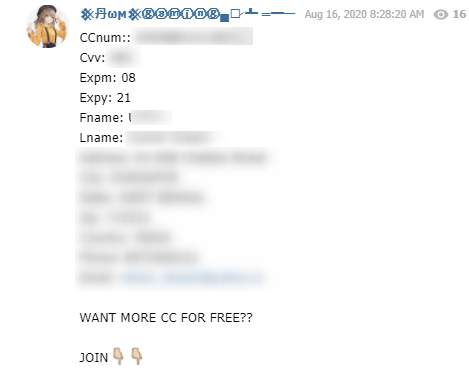
Leaked credit card information in HackingwithAndroid Telegram Group from the Webhose cyber endpoint
Advanced Dark Web Monitoring is Key to Modern Brand Monitoring
Cybercriminals have a number of options for communicating with their audience: social media, the open web, and the deep and dark web. Social media analysts responsible for brand monitoring today need to be able to constantly monitor all of these different types of sources. Advanced dark web and data breach detection services, such as Webhose, are able to deliver comprehensive coverage of these different sources. They can also detect the most relevant groups or channels in chat applications. These advanced tools can assist enterprise organizations in monitoring their brand, despite the ever-expanding sources and channels these cybercriminals exploit.
Discover the new project
How does third-party data get from the source to the end user? Follow the exploration at the Data Market Study, also sharing discoveries and insights in a newsletter.
Sponsors